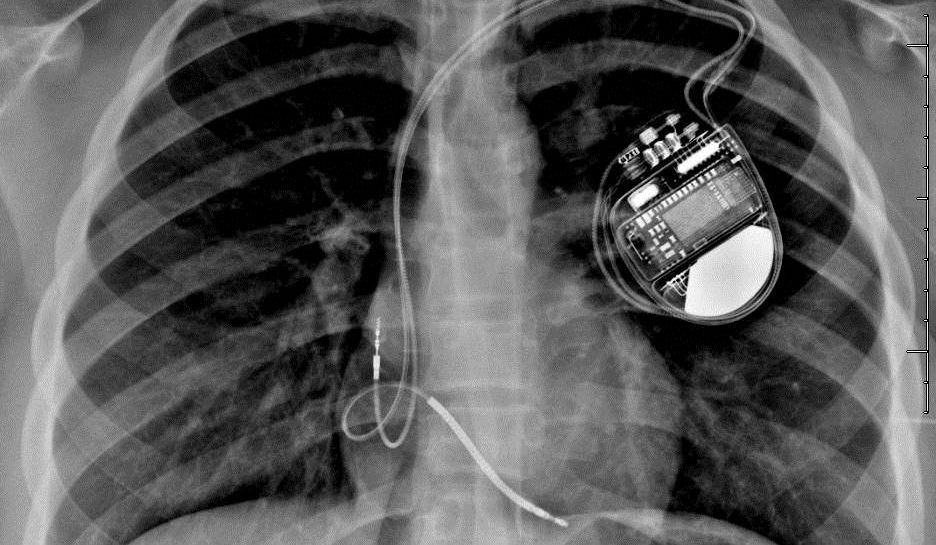
"It's basically industry best practice," says Schneier. "But without enforcement, it's just pleading."
Critics are concerned that the responsibility is still primarily left up to manufacturers to disclose when a device has been hacked.
Consumer Watchdog president Jamie Court says recommendations are not enough and we won't see new laws until public officials are affected. "All its gonna take is one congressman’s defibrillator being hacked and we’ll have some new laws really quickly," according to Court.
The FDA is taking public comments on its guidelines until April 21.
Read on to see three real life situations the FDA guidance is designed to prevent.
Security Experts Hack a Surgical Robot
 Remote surgery—where a surgeon in one location controls a medical robot in another—is extremely useful in places that don't have trained medical experts.
Remote surgery—where a surgeon in one location controls a medical robot in another—is extremely useful in places that don't have trained medical experts.
For these long distance operations, doctors often use a low-quality connection to the internet, or even wifi. But researchers at the University of Washington proved they could hack into these public communication systems that control teleoperated robots.
They accessed the network that controlled the robot and disrupted the signals, making the robot’s movement jerky and difficult to control. And by moving the robotic arms too quickly or beyond a predetermined point they could get the robot to shut down completely.
If this had occurred during an actual life-saving procedure the outcome could have been fatal. Fortunately the researchers also figured out ways to encrypt the device—the exact type of precaution the FDA encourages in its new draft guidance.
Hacker Proves He Can Kill a Patient Through a Drug Pump
 In 2013 cybersecurity expert Billy Rios remotely hacked into a Hospira infusion pump. The pump releases controlled amounts of a substance and can be used to administer insulin to a diabetic or chemotherapy drugs to a cancer patient.
In 2013 cybersecurity expert Billy Rios remotely hacked into a Hospira infusion pump. The pump releases controlled amounts of a substance and can be used to administer insulin to a diabetic or chemotherapy drugs to a cancer patient.
They're found in almost every hospital and usually sit next to a patient's bed. Hundreds of them can be monitored and controlled from a central station in the hospital.
Rios ordered the pump off of eBay for $100 and was able to figure out the device's pre-programmed password by reading its technical manuals. This information, in conjunction with knowledge about the device's software and what network it was operating on was enough to give him access.
He then proved he could remotely administer a lethal dose of drugs through the Hospira pump. Luckily Rios is a benign or "white hat hacker" and turned over his findings to the Department of Homeland security. His report galvanized the FDA to issue its first warning about a medical device.
Hackers Demand Ransom for Medical Records
 When 4.5 million UCLA medical records and 78.8 million Anthem medical records were hacked it made major headlines.
When 4.5 million UCLA medical records and 78.8 million Anthem medical records were hacked it made major headlines.
But smaller healthcare organizations aren't immune and one incident, north of Chicago, resembled a bank heist.
In 2012, Surgeons of Lake County, a small medical practice in Illinois, fell victim to a digital data breach.
Hackers accessed the practice's server where e-mails and more than 7,000 electronic medical records were stored. The hackers then encrypted the files and demanded a ransom.
The doctors refused to comply and alerted local authorities. They also offered free credit monitoring services to patients following the attack.
The medical practice would not discuss the investigation. But the practice issued a press release to alert the public and the Department of Health and Human Services included the hack on its website, which lists breaches affecting 500 or more individuals.
The good news—the FDA says it hasn't received any reports of fatal cybersecurity breaches, which hospitals and device makers are required to report.